Screen Shots:
 Ran into this bad boy today. I was reviewing the code from the github dump i found here: https://gist.github.com/hasherezade/628928248e8e6c8dae04#file-config-json-L453
Ran into this bad boy today. I was reviewing the code from the github dump i found here: https://gist.github.com/hasherezade/628928248e8e6c8dae04#file-config-json-L453
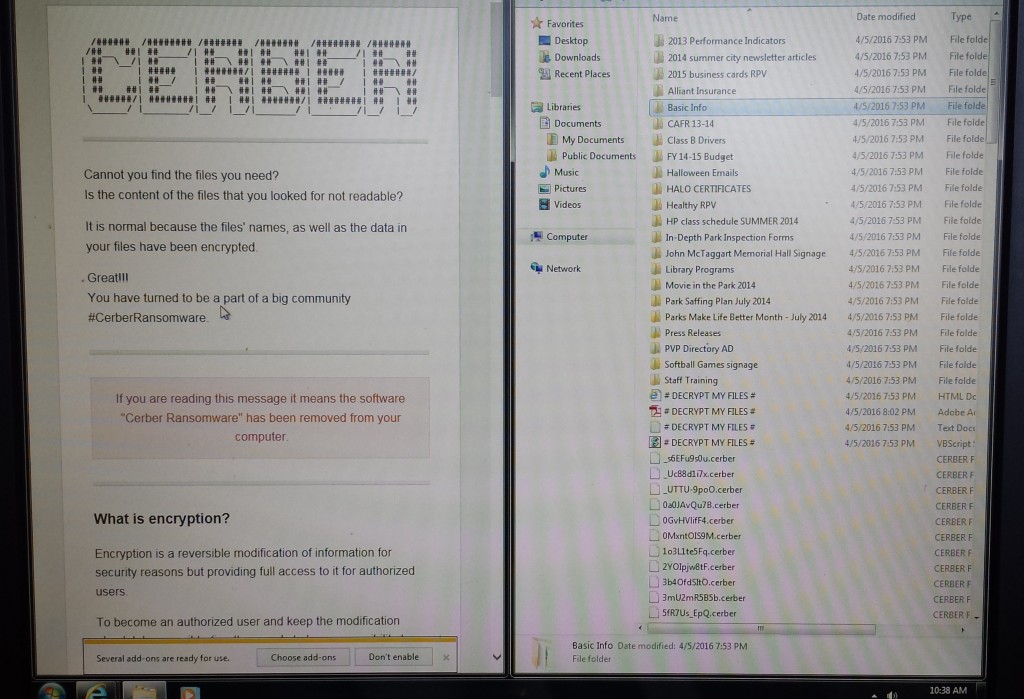
I was concerned that it worked on also infecting file shares but from what I can see it doesn’t touch them. After having a user infect a computer here in our Network it looks like nothing else has been touched but all the files on her computer displaying messages like this:
Every file basically encrypted until you pay the son of aguns.
Basic Steps on handling this type of problem:
- Verify none of your other networked file shares have been infected and run a full virus scan of the shares just to be safe. So far I haven’t heard of Cerber jumping to any networked shares so it keeps things local to the machine which means it is mainly targeting end users. Here is a snip of Code from the above link that leads me to believe it is only keeping things local since it’s the only reference to any directories it makes: “folders”: [
“:\\$recycle.bin\\”,”: \\$windows.~bt\\”,
“:\\boot\\”,”: \\drivers\\”,
“:\\program files\\”,”: \\program files (x86)\\”,
“:\\programdata\\”,”: \\users\\all users\\”,
“:\\windows\\”,”\\appdata\\local\\”,
“\\appdata\\locallow\\”,”\\appdata\\roaming\\”,
“\\public\\music\\sample music\\”,”\\public\\pictures\\sample pictures\\”,
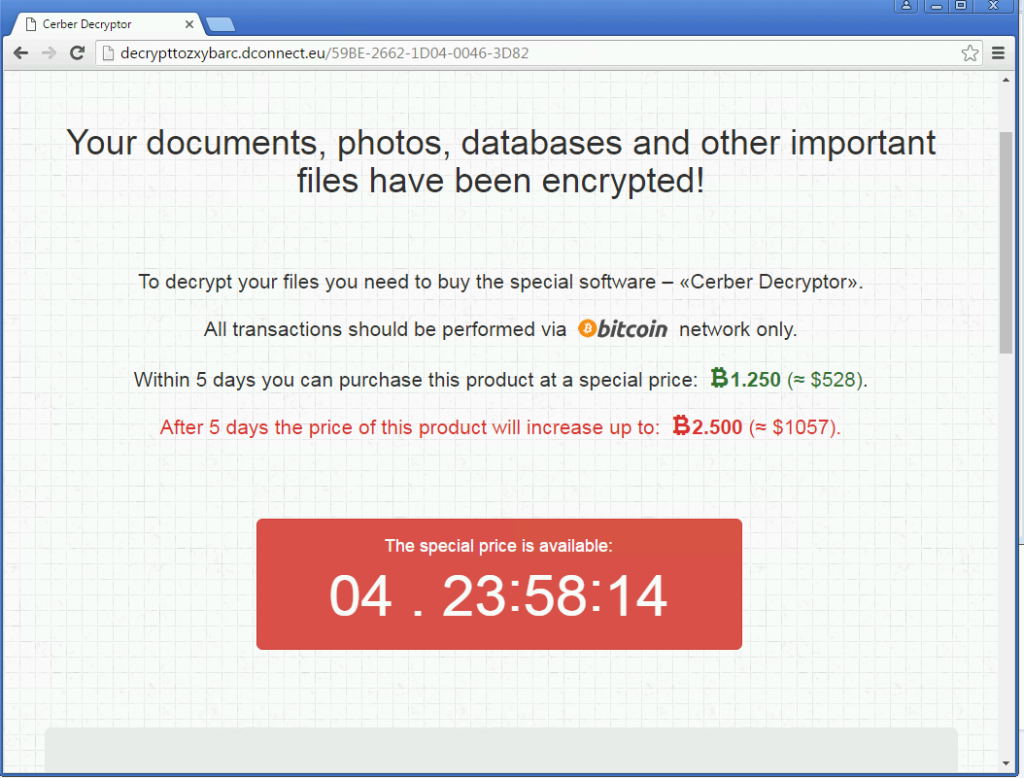
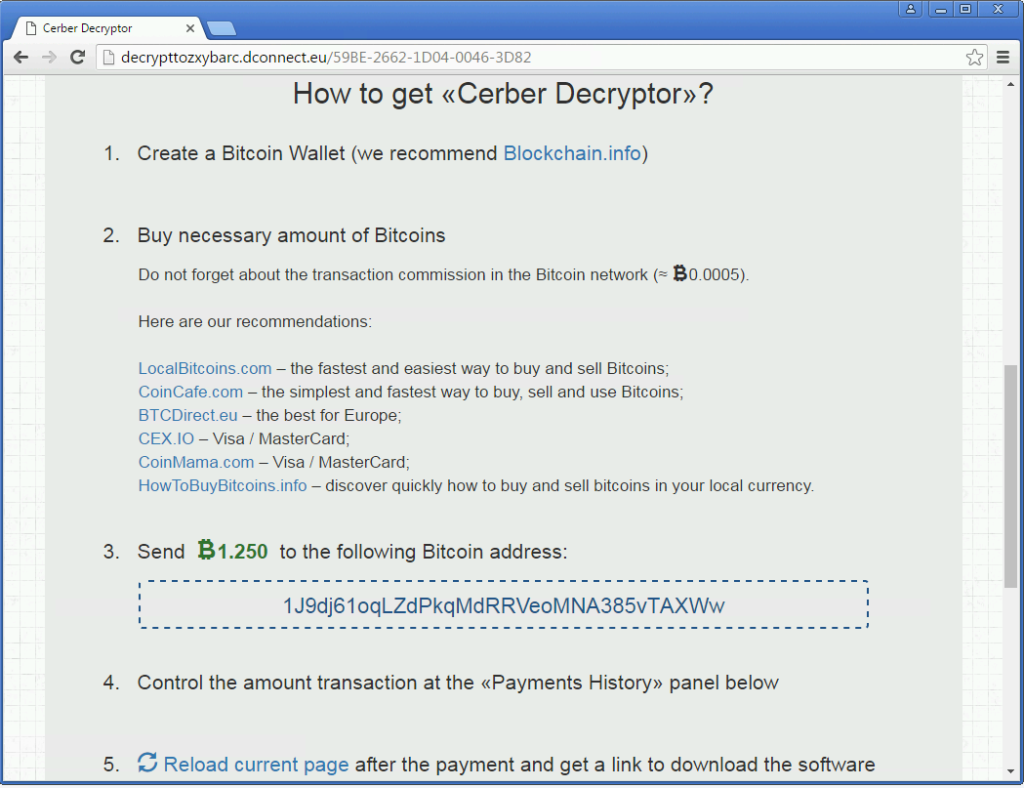
“\\public\\videos\\sample videos\\”,”\\tor browser\\ - Next step is to Burn the infected machine(Just re-image it) Users might ask for the files in which case they can pay the ransom if it’s that important. Something like 2 bit coins or $500 if you pay up before it doubles on you every week. One other thing users have asked me is if they can at least see the files they lost in which case your going to be taking a picture of the computer screen because there’s no safe bets I would take making any kind of digital bridge to that computer(ie: plugging in a usb stick or taking a snapshot to transfer to a usb Stick)
- Final step is replace the users PC and restore their files. That is if you back them up!
UPDATE:
Confirmed with Talos Security group that this is not de-cryptable as of yet